ARP poisoning or spoofing is kind of like being a spy behind enemy lines.
As a matter of fact… it is JUST like the spy in Team Fortress 2.
“He’s already broken the defenses
Have you seen what’s he been doing with our friends…
The worst part is… he could be any one of us”
~ The BLU Spy… on the subject of The RED Spy – Team Fortress
In Team Fortress 2 the cool, calm and dressed to kill, inhaling that smoke like his life depends on it, The Spy goes behind the enemy lines to get in physical proximity of his target—making himself invisible, then disguising himself to look like any one of them, to listen to what is happening and then take action when/if deemed necessary.
ARP poising is the personification of his actions in a computer network.
It happens when someone, usually a hacker, connects into a network and then tries to get registered as someone else. Afterward, they can:
Sit there listening, monitoring the traffic going through, analyzing and learning, or
- Block it if they want to,
- Or perhaps redirect it to someone else, inside or outside the network
This, in turn, becomes a small part of a larger scheme resulting in usually a phishing or DOS attack.
The process is also called ARP spoofing.
Let’s take a deeper look…
ARP
If you are a bit familiar with networking, then ARP is one of many common terms you deal with on a day-to-day basis.
It is Address Resolution Protocol, which connects the Link Layer with the Internet Layer. It does it by helping to connect an IP address, used to identify devices on the internet, with their respective MAC Address.
A Media Access Control address is a unique address consisting of six pairs of hex digits. It is designed to be unique and contains information about the manufacturer. The MAC address is hard quoted on the device and cannot be changed.
The IP Address, on the other hand, is given to a computer/device. IP addresses used to be 32 bit long and have evolved to be 48 to 64 bit long. IP addresses and MAC addresses are different in appearance and design. IP addresses are dynamic and can be changed.
How Does It Work?
Imagine a computer sending data to another computer. What is happening underneath is that data is being divided into standard packets of smaller size and are then sent for the destination. The packets have the domain names of both the source and the destination computers.
The destination computer’s IP address is identified by looking it up in the DNS table. The DNS table has all the human understandable address names and their associated IP addresses…
So, once the IP address is obtained, the data is routed to the destination.
Now: We know now the IP address, but we have no idea which MAC address is associated with that IP address. These are machines with physical addresses. The IP address may provide a logical virtual address to the computer, but it has to be mapped on the physical network.
So in a network following the ARP, the sending computer will now look at the cached ARP table…
- Here there will be MAC addresses associated with IP addresses. Once found, data can be sent to the destination device/computer.
- Or: If there is no entry found, the computer will simply announce a request to all the connected devices with the required IP address. In response, the computer having that IP address will respond back with its MAC address.
Once the computer has the MAC address, it now has all the components to identify the destination computer, i.e.
- Domain name
- An IP associated with the domain name
- And the MAC address associated with the IP
It will now send the data divided into packets to the destination.
The broadcast message is sent to the ff.ff.ff.ff.ff.ff address. The cached ARP table resides at the switch, connecting the network.
Old Protocol
ARP is an older protocol designed to be efficient above anything else. Perhaps this is why it can be easily exploited.
There have been advancements though, but merely to compensate scenarios for requesting updates.
The ARP typically generates request/response messages. The advancement here was in the form of a different kind of message—an update message, which is sent to all the devices to updated their cached ARP tables.

This update message is called the Gratuitous ARP. The reason for this advancement was to reduce unwanted requests for MAC addresses on a network. It is used when…
- There is a need to update MAC addresses on the switches
- There is an update of any MAC address associated with an IP address due to perhaps an introduction of new hardware
- Or when there is IP address conflict in the network
ARP is a protocol without any states and authentication. The ARP table is simply updated whenever it receives packets in a new reply. Even if the new information is about addresses already stored in the ARP table, it will still be updated. This fast and efficient way of operation is also the reason for its weakness.
So now that we know how the ARP works, generally, it is now time to get all Shakespearian on that network:
ARP Poisoning or Spoofing
We have already learned that ARP poisoning or spoofing is when one computer or device pretends to be another computer on the network.
It does so by tricking the network into believing that its MAC address is associated with the target computer’s IP address. The ARP table is compromised and all communication directed towards the targeted computer is instead sent to the device/computer pretending to have its IP.
Here is how all that happens, broken down in simple steps…
- In the first step, the attacker/hacker gains physical access to the network.
- Once connected to the network, the attacker then starts listening/receiving communication with the help of some software tools. These tools set the connected device’s IP address to the subnet of the target computer’s IP address.
- Gaining knowledge by listening to the communication, the attacker gets all the IP and MAC addresses of the devices connected with the network.
- After gaining this information, a target is selected and then the attacker starts sending ARP data on the network which seems to be going to the target’s computer. Here, with the help of software, the ARP data is corrupted so that it contains the IP address of the target computer but the MAC address of the attacker.
- Due to the non-authentication nature of the ARP protocol, the network simply translates the data and starts associating the IP address with the MAC address of the attacker.
- The ARP table is refreshed with the new information and the data packet traffic meant for the targeted computer (victim) gets sent to the attacker device/computer.
- Once that happens, the attacker can simply receive or modify data, stop it or maybe hijack the network.
The choices after a successful attack are vast. Here we discuss a few of them…
Man-in-the-Middle Attack
The man-in-the-middle attack is simple. It happens when the attacker becomes a listener by pretending to be any two parties of the network and letting the data between them pass through it after scanning.
Here, the information collected can be used to step into the communication at the right time, pretending to be the other party to both sides.
DOS Attack
The Denial of Service attack is one of the most common attacks that attackers use. In it, the attackers, after ARP spoofing, associate a huge number of IP address with a single MAC address.
This results in a large enough traffic that can’t be handled by the targeted party, which results in the target getting overwhelmed by the incoming traffic in such a way that it cannot perform any other task.
Imagine a server computer being a target of the DOS attack, it will be too busy to handle any request and will effectively be denying to serving any of the incoming requests, hence the term, Denial of Service.
Session Stealing
In Session Stealing, an advanced and higher level attack, the attacker after gaining access to the network, continues to monitor the data and scans for session IDs and cookies. These cookies contain data that keep a user logged in to a website during their visit. Once the attacker has that information, they can get access to the target user’s accounts.
If you missed it, the monitoring part is done with the help of ARP poisoning.
So, in short…. ARP spoofing is a dangerous attack method that works by mimicking someone else for the ultimate goals of the attacker, to effectively kill the target by overwhelming them with the brute force of data requests, affectively poisoning their food by intercepting their data.
If only we knew how to detect it… we could perhaps stop it.
So, do we?
Detecting ARP Poisoning
In smaller networks, detecting these attacks is easy. You just need some wits, guts and a set of eyes that can read multiple numbers without getting dizzy easily.
Usually, all you need is a command prompt with knowledge of DOS commands, perhaps a free packet analyzer or maybe just a premium tool.
But let us not get ahead of ourselves… let’s just see how we can do it.
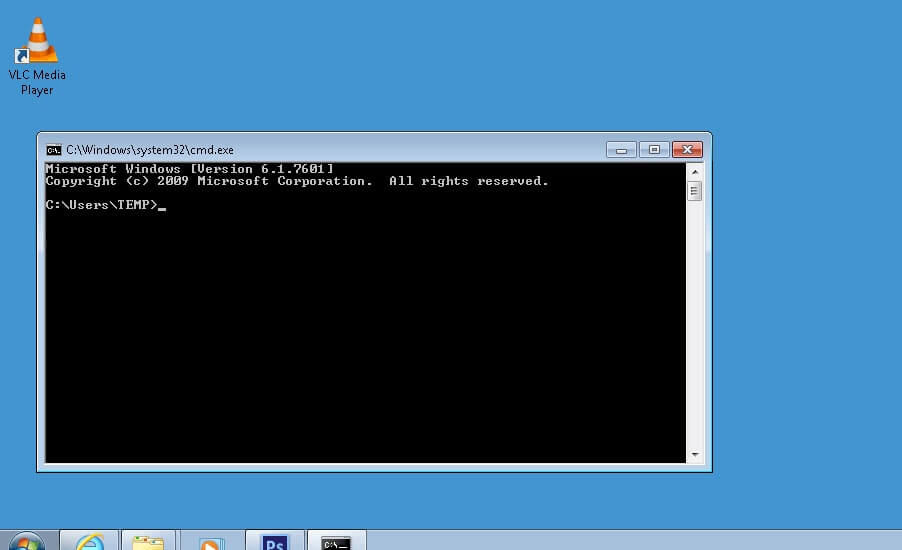
Command Prompt
Open up the command prompt on your Windows device. You can do that by typing ‘cmd’ in the run or search box of the Windows Explorer.
Write the following DOS command and press enter.
- arp -1
The result will display a table of IP addresses associated with their respective MAC addresses.
Here look for any duplicate entries for IP address which may be pointing to multiple MAC addresses.
Typically, as a result of ARP spoofing, there will be ideally, at least two MAC addresses associated with a single IP. There can be more, pointing to different kind of attack strategies.
This is a beginner-level detection process which may or may not work. This means that while it is possible to detect such entries, it is possible that your network may not be under attack. There are some legitimate scenarios where duplication occurs.
However, if you see this, you can be prepared and start moving towards further actions for prevention or advanced level of detection.
Using a Packet Analyzer
Packet analyzers are software that are used to monitor packets of data. However, using such tools requires you to be familiar with what you are working with. If you know what you are looking for, you will be able to find it.
Wireshark is a widely popular analyzer tool. It is used to scan, monitor or analyze what is happening at the network level. Wireshark gives you a HUGE array of options, so it’s best to learn how to use it properly first or let someone else with more experience do the analyzing part.
Detecting the attack is not enough—we must also prevent it:
The Cure for Poison: Preventing ARP Poisoning
The best defense is offense… but that is not an option here. Therefore, we’ll need to go with the next best thing: Prevention.
There are multiple ways of doing this, each with their own pros and cons. We will start with the simplest one of them:
Static ARP Entries
The ARP entries in the ARP table are done both dynamically and statically. Dynamic entries are the ones which result in data being overridden after a reply is received with new information. Since any update can override previous data, spoofing is easy.
The cure is having only static entries in the table.
This works by having the static entries to be set as read-only on host machines. Now the data can only be read but not be written upon automatically. Almost all kinds of simple ARP spoofing/poisoning attacks can be prevented this way.
However, there is a drawback.
This can only work on smaller networks since the work required to enter, maintain and then update the static entries would be tremendous and realistically impossible. It’s a huge manual task.
ARP Spoofing Detecting/Prevention Software and Packet Filters
We mentioned traffic monitoring software that gives the user an inside view of the communication without any filters. These packet filters and spoofing detecting and preventing software are a step ahead.
Mostly used by network admins, they analyze ongoing traffic packet by packet and determine which ones are good to be transmitted or not. This happens by identifying certified packets, which are certified by some mechanism to be marked as authentic on the network, and, by analyzing request and response packets. Whatever is found uncertified or out of line with the request-response analysis is discarded.
Encryption and VPNs
The use of encryption software during communication may not exactly prevent the spoofing. It will, however, secure the data from being read by the attacker and you will be pretty much secured from the simpler form of attacks.
Using the HTTPS protocol while being on the internet whenever possible can help during all the other times you and your data are still vulnerable. Attacks like Session Stealing can still affect you.
Having a good Virtual Private Network is another layer to the encryption you can add to be properly secured from data theft. Once again, you are not just preventing the attacker; you are effectively stopping them from reading your data, even your IP address.
Not only all your traffic will be encrypted but anyone outside of you and your VPN server will not be able to read it either. This makes it a perfect solution for a user who is not a web/network admin and has to think on their toes.
Operating System Level Prevention
Having expert knowledge of the operating system the network is running on can sometimes help to solve simpler attacks.
Operating systems behave differently when handling communication, e.g.
- Linux simply ignores any ARP reply data which is not initiated. It updates its cache table when it reads a response generated in the result of a request by another machine.
- In Windows, you can modify registry entries to change the default of how ARP cache behaves.
- The Sun Microsystem’s Solaris simply updates the ARP cache data after a certain time period.
Use What You Can
There is a common theme among the options we have shared while familiarizing you with the problem:
None of them is perfect… on their own.
Some are too laborious, some are static, rigid to be exact, to follow and hence require a lot of work. Others are not completely foolproof, some work on a smaller and even personal scale, and then there are some which require a degree of technical know-how.
So see what fits best for your situation and choose wisely. Employing the combination of identification, prevention and security techniques may give good coverage from the probable attack.
However… when the task seems too technical or complex, share it with industry professionals and invest in premium solutions.