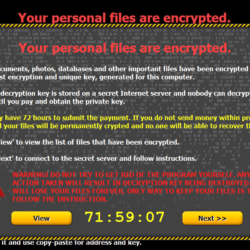
In the previous article we discussed the new PolloCrypt, Breaking Bad ransomware and showed you how it works. But today we provide you with the…
Category: Security News
Recent news about things happening in the field of cyber security. Catch up with the latest security and hacking news
PuTTY SSH Client Contains Trojan and Steals Information
Putty holds important place in system administrator’s toolkit as it allows encrypted connection to remote servers. But today Putty ssh client injected with trojan appeared…
Document Based Malware Software Tool – Microsoft Word Intruder
Microsoft Word Intruder According to nakedsecurity the new tool Microsoft Word Intruder or MWI allows anyone to develop a high level malware software. It is thought…
VENOM Vulnerability
What is Venom Vulnerability? VIRTUALIZED ENVIRONMENT NEGLECTED OPERATIONS MANIPULATION or VENOM vulnerability has been uncovered by crowdstrike. According to senior security researcher Jason Geffner this…
Cyber Attack on Bundestag
According to Spiegel the national parliament of Germany, Bundestag, has been targeted by a major cyber attack allowing unknown perpetrators to penetrate internal network. According to…