In February 2018, Kaspersky Lab discovered the latest threat to our internet security is a type of malware called “Slingshot.” The fascinating part is that this virus does not live in our computers or cell phones, but – in routers.
The origin of Slingshot is still a mystery, but it’s known that it somehow managed to stay under the radar since 2012.

The team who discovered the malware named it Slingshot because they came across the word unencrypted in some samples of the code.
Around 100 users have been affected by this malware until now, and none of them are from the U.S. Reportedly, the Slingshot malware aimed individuals from Africa and Asia. Almost all of the victims used MikroTik routers.
How Slingshot Malware Operates
Slingshot operates from routers, filtering and collecting all the data that goes through it. It has insight on users’ keyboard strokes, passwords, data, USB connections, screenshots, clipboard data, and much more.
After encrypting the data, Slingshot sends it to the server run by the individual or group who is operating the malware.
Let’s break down the entire process step-by-step:
- A person buys a compromised router, or the malware somehow infects the router.
- Slingshot then replaces the direct link library with malicious code.
- The malicious code has system privileges and thanks to that, Slingshot is able to gather information.
The malware attacks kernel-mode and user-mode modules on victim’s computer, which allows it to exfiltrate, encrypt and send all the data mentioned above without anyone noticing that something unusual is happening.
Given what is known so far, one can only imagine how much money, time and expertise it took to create malware so complex and sophisticated.
One question, in particular, comes to mind…Who is operating the malware?
Who Stands Behind Slingshot?
According to Kaspersky Lab, the creators of Slingshot are probably native English speakers. Experts even managed to find some references in the code to prominent writer J.R.R. Tolkien. Furthermore, the team claims that the group of coders who created Slingshot is highly organized and well-funded, which may imply government involvement.
But what is the motive? Keeping in mind that the victims were targeted individuals from Africa, Asia and the Middle East, one can only assume that the primary purpose of Slingshot is espionage. Users from the West are safe for now because MikroTik routers are not generally popular in the United States and Western Europe.
How to Know If Your Router is Infected?
There is a way to find out whether your router is infected with malware or not, although you can’t really say for sure if it’s Slingshot that infected your router.
On the other hand, it doesn’t hurt to check if your DNS server is changed by following these steps:
- Go to your router’s setup page. In my case (for my Cisco router) I will have to type in 192.168.0.1 in my browser.
- Enter your credentials (username and password). If you do not have a password, you can leave this field empty. Also, if you have forgotten your credentials, contact your internet provider.
- Click on DNS settings.
- If DNS is set to automatic or disabled, everything is fine. However, if it is set to manual, your router might be infected with malware.
- To be sure, Google the DNS server address to check if it is authentic or not.
How to Get Rid of Slingshot?
If you have detected malware on your router, all you can do is reset it or restore it to a previous version. Also, disable remote access and change your router’s password.
You can also manually reset your router. Keep the device off for 10 seconds and then turn it back on.
Arguably, it may be naïve to think that the creators of Slingshot did not think this through and that a simple “turn it off and on” will do the trick. However, there are certain steps you should follow if you want to keep (or at least try to keep) your device malware-free.
How to Stay Safe from Malware?
- Always update your router.
- Use a VPN (Virtual Private Network) service.
- Disable remote access.
- Change the password (router, not Wi-Fi password) by going to Setup/Quick Setup.
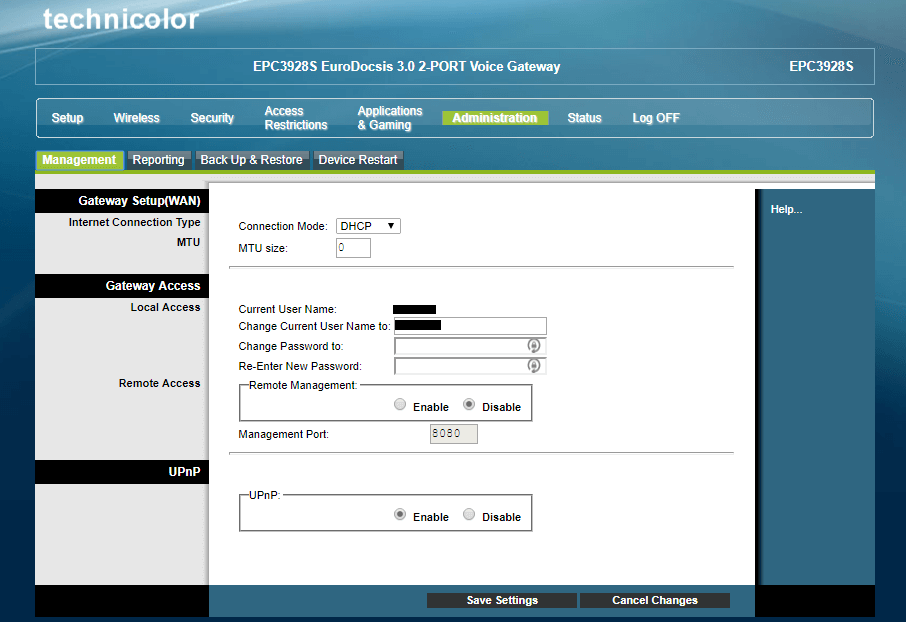
- Disable UPnP by clicking Administration/ Management. As you can see, it is enabled on the router represented in the screenshot.
- If you are a business owner and one of your employees notices something odd, make sure to hire a professional to investigate a potential security breach.
- Educate your team about the latest malware and how to fight it, or rather: how to avoid activating it.
- Use the latest security systems and
Even if you are not a MikroTik user, following these tips will not do any damage.
According to Kaspersky Lab, not all of the victims of this sneaky malware used MikroTik. It is always a good thing to update the router at least every two months.
Here is a simple guide on how to update a Cisco router:
- Type in 168.0.1 in your internet browser.
- Enter your credentials.
- If you do not have a password, just skip this step.
- Click Administration/ Management/ Back up or Restore.
- You can also click Device Restart
Unfortunately, my device does not have an Update Firmware option. The newer products do, you’ll likely be able to update your router if it is a later version.
As you can see, the process is pretty much self-explanatory, and can save you a lot of trouble.
The Bottom Line
Slingshot seems to be a successful malware program since it managed to go undetected for six years. What organization or individual stands behind this malware remains a mystery for now, as is specific instructions on how to detect or remove it.
Presently, the only thing you can do to respond to the risk is to follow certain general steps to keep your router relatively safe. For instance, always keep your device up to date, disable remote access, change your router’s password and disable UPnP.
Another comforting thought (to some extent) is the assumption that regular folks are hardly people of interest, for it is speculated that the Slingshot malware is most likely used for espionage targeting a specific group of users.