How BitTorrent Mitigated DRDoS Vulnerability
In previous week we published an article about how it was possible to initiate a BitTorrent DRDoS attack using UDP protocols. In that post security researcher Florian Adamsky and his team reported on the possibility of exploiting BitTorrent protocols for Distributed Reflective Denial of Service Attacks (DRDoS).
The main idea behind this finding is that cyber attacker is able to exploit any user secretly while directing their traffic to a potential victim in a way that would kick a victim’s system offline or DoS them.
On August 27 BitTorrent reported that:
Thankfully, no such attack has yet been observed in the wild and Florian responsibly contacted us to share his findings. This gave our engineering team the opportunity to mitigate the possibility of such an attack.
How does libµTP work and what can be done for mitigation
According to BitTorrent engineers and their blog post by Francisco De La Cruz the efficiency of DRDoS attack using BitTorrent environment is measured by amount of traffic that can be forwarded to a victims system or Bandwidth Amplification Factor (BAF).
Most of the popular BitTorrent clients use libµTP. libµTP is able to detect network congestion and independently throttles itself upon detection. The main flaw in libµTP is that user’s systems might be secretly used to amplify attack due to the way libµTP handles incoming connections.
Below illustration shows that an attack starts attack with a SYNchronize with sequence #209 and acknowledgement #0.
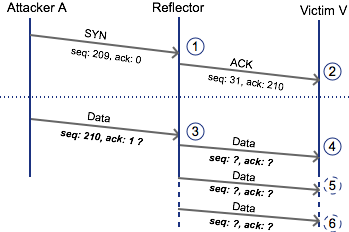
Above illustration can be described with following steps:
- Reflector receives connection packet #209 and is expecting #210 as a next packet. Reflector informs Victim V by sending acknowledgment (ACK) packet with next sequence number, in this case its #31.
- Attacker needs to send a BitTorrent protocol header. In order to build a proper one he/she needs to provide an ACK number of the last received packet at stage (2).
- The flaw in libµTP would allow the reflector to accept any acknowledgement number at (3) allowing the attack to be carried out. A mitigation relies on the fact that it would be fairly difficult for an attacker to guess the acknowledgement number at (2) for a sufficiently large number of reflectors.
BAF can be reduced and even be mitigated by “enforcing the requirement for a potential target reflector to receive a unique acknowledgement number when receiving traffic“. Thus guessing the acknowledgement number becomes a real head ache for any attacker. Using a reflector ensures that the packets outside of allowed windows are dropped and they will never reach victims system.
According to BitTorrent blog post:
As of August 4th, 2015 uTorrent (3.4.4 40911), BitTorrent (7.9.5 40912) and BitTorrent Sync (2.1.3) clients using libµTP will now only transition into a connection state if they receive valid acknowledgments from the connection initiators. This means that any packets falling outside of an allowed window will be dropped by a reflector and will never make it to a victim. Again referring to the diagram above, this means that (3) is dropped and (4), (5) and (6) never make it to the victim. Since the mitigation occurs at the libµTP level, other company protocols that can run over libµTP like Message Stream Encryption (MSE) are also serviced by the mitigation.
Special thanks to Christian Averill for providing this information
