Phishing

Phishing activities are on the rise. All those aspiring to steal login details for different websites can do it quickly and easily through a phishing-as-a-service platform called Fake-Game that has recently emerged.
The platform is said to be a successful online site for those people who are interested in getting login credentials for various online accounts through phishing.
The site proves to be advantageous to its users because it doesn’t require training or previous experience.
According to a cyber security research company called Fortinet, the site allows one to obtain the user and the password of a given account without much technical knowledge.
The site has been in operation for a considerable period dating from around July 2015. What makes it so popular then? The site even has its customer support and tutorial videos.
That makes it incredibly user-friendly for new users.
How the phishing platform works
Fake-Game uses a business model like that used by malware-as-a-service and ransomware-as-a-service. Therefore, the users can generate renewable income quickly.
The site has been offering phishing facilities for the users who signs up onto it.
Fake-Game itself generates revenue through VIP subscriptions that it offers to its users. Typically, the services have lowly prices.
There are also more benefits that accrue to the VIP users that do not accrue to the one-time users.
An example of such privileges is the ability of the VIP users to browse all other phished accounts.
Examples of pricing schemes include a $3.50 monthly subscription, $5.70 and $7.12 for two-month and 3-month subscriptions respectively.
How to successfully hack using Fake-Game
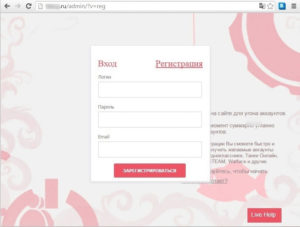
The website has an established easy to use interface that allows the users to execute their next steps. First of all, the site opens a window that displays some instructions.
They include but are not limited to the mode of phishing that is; the person from whom you want to steal credentials will input them into your fake site.
It also provides definitions of terms that are frequently used in the process of phishing.
The next window will ask one for the site whose credentials they want to steal. It then will create an affiliate page of the clients of Fake-Game to which the credentials will be sent.
Even Fake-Game provides the user with a framework to execute their hacking, they (the hackers) have to use some tricks to tempt their victims to provide their credentials.
Those prompts lure victims to help hackers accomplish their objectives efficiently and smoothly.
Validation of credentials

Fake-Game’s phishing page has a mechanism for checking the validity of credential. Once the valid credentials have been entered, the page responds with a comment like “good” to verify the credentials.
Such framework is attractive for the clients of Fake-Game.
What next after obtaining the credentials?
It doesn’t matter which site one wants to hack. The site provides the framework to many sites.
Once the credentials are obtained, the hacker can sell them to other people who may want to use them or sell them to an online criminal marketplace to where Fake-Game may direct them.
There is a barrier to entry into phishing business
However, for those who aspire to make a living from piracy, it is not as easy as it looks to penetrate the market barriers that have been put in place by Fake-game.
That in itself hasn’t stopped the business model developed by malware and other phishing tools from spreading.
Different mechanisms are being developed although there are chances that some have been developed in other parts of the world already.
Such phishing platforms have availed login credentials to almost everyone. The end-result is a serious threat to the privacy of online personal and business accounts.
It is high time that most firms and everyone invest in creating awareness and taking caution.
Final purport

Cyber-attacks are rapidly becoming dangerous. Users’ accounts are more vulnerable to phishing attacks than they were a few weeks ago.
It is important that users take caution and invest in tools to detect such phishing threats.
It is appropriate for your firm to run IT security checks to determine which accounts are prone to phishing attacks before undertaking the necessary measures.
